Appearance
中间件风险评估
IIS
文件目录、文件下载
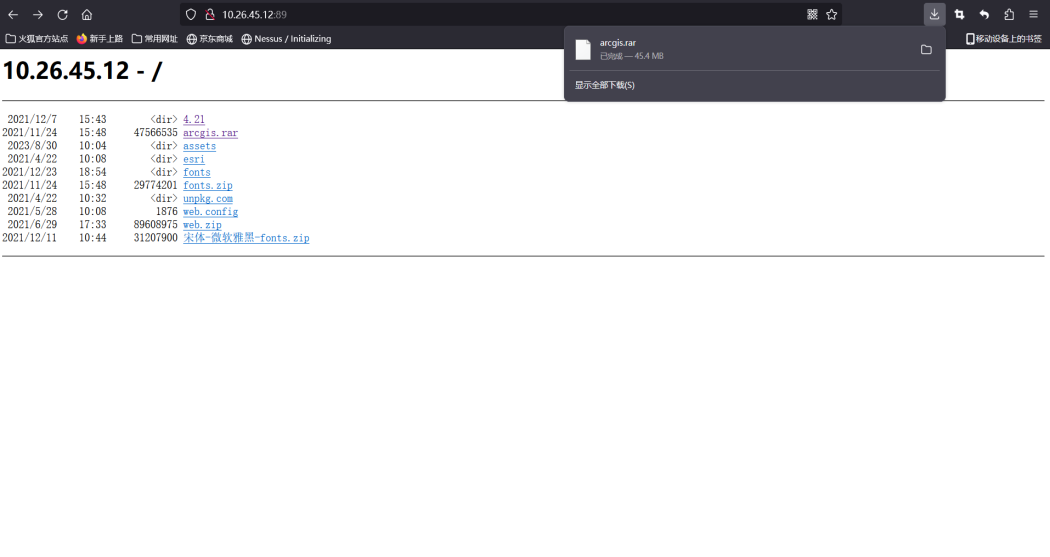
建议:禁用iis目录浏览功能
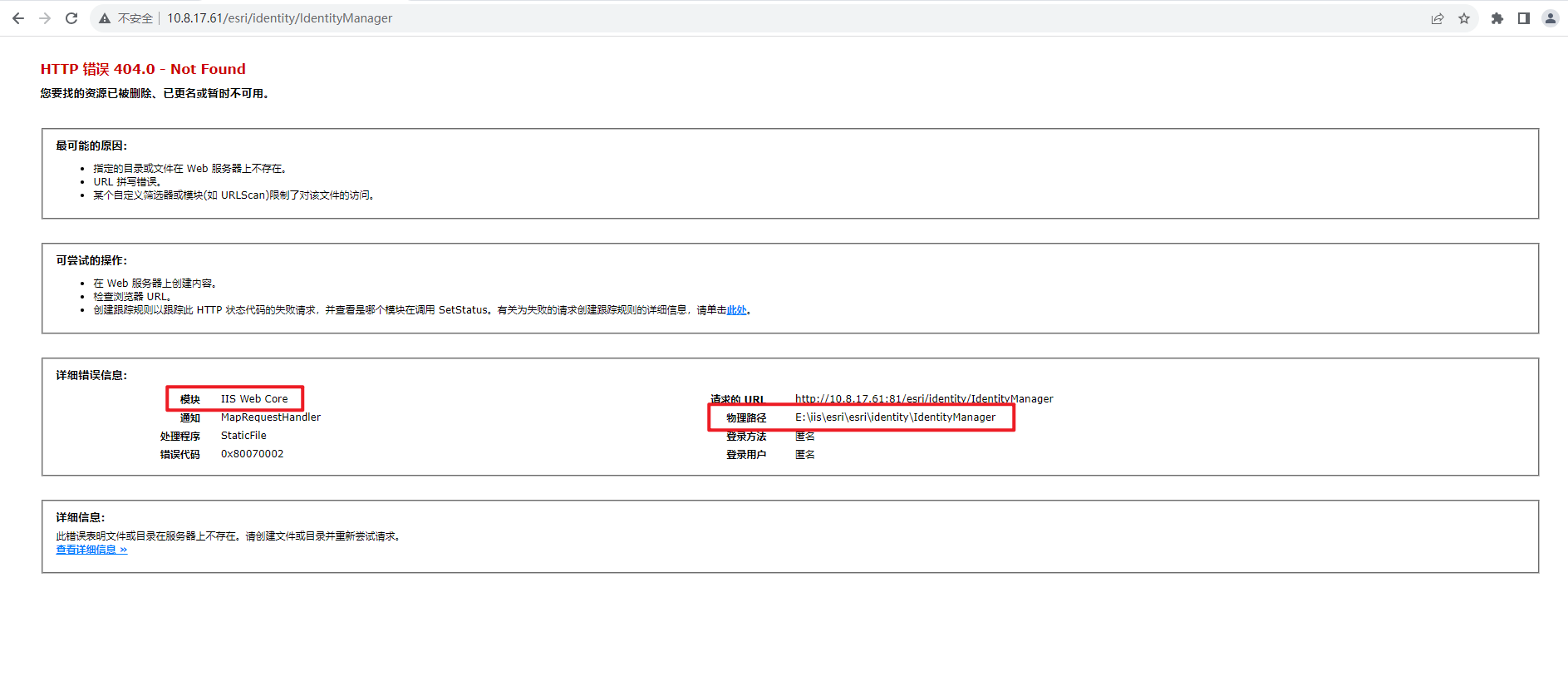
用户信息泄露
iis错误页面,会显示物理路径
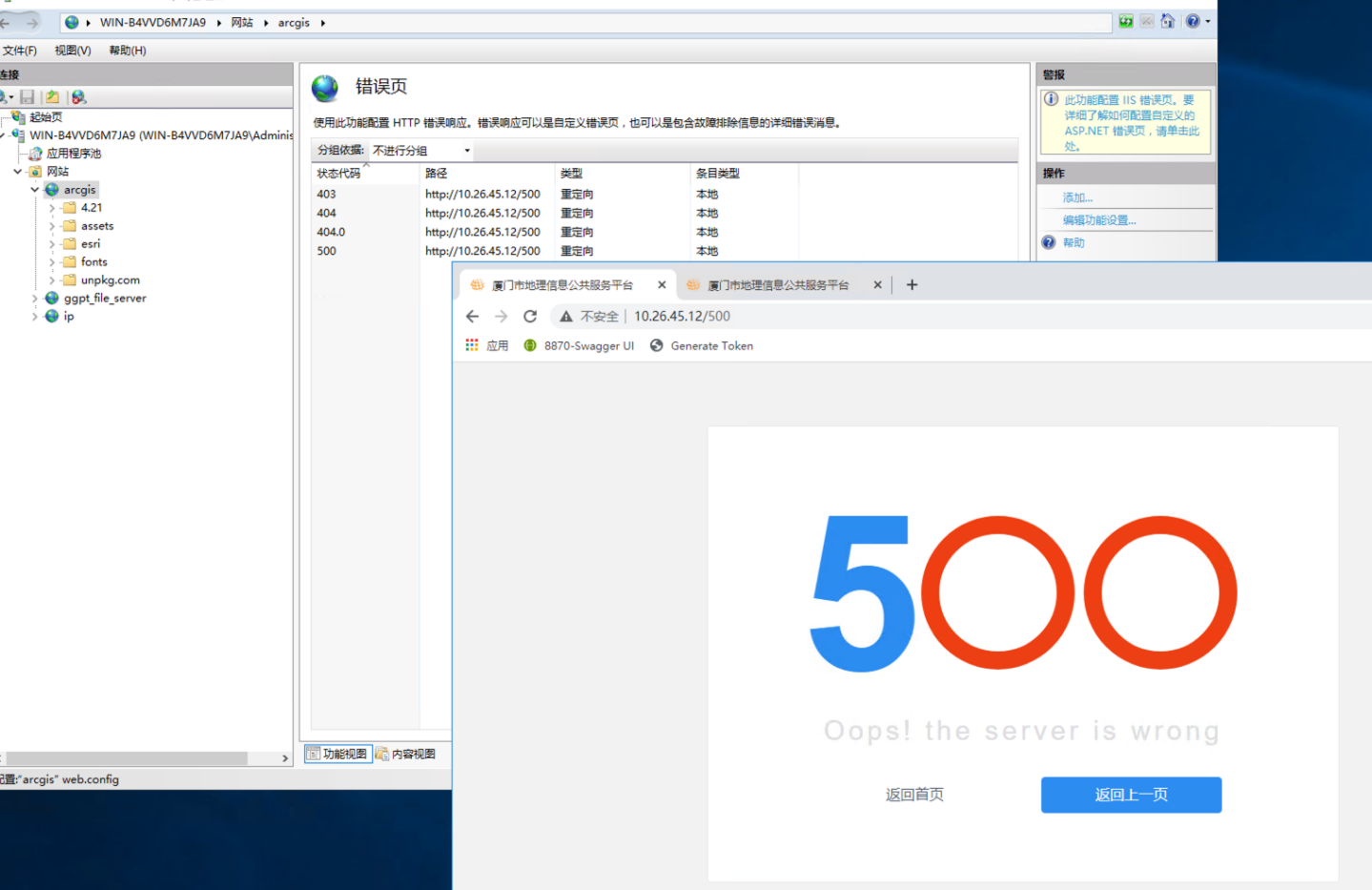
建议:重定向iis错误页面,定到系统的500活着404页面
Redis
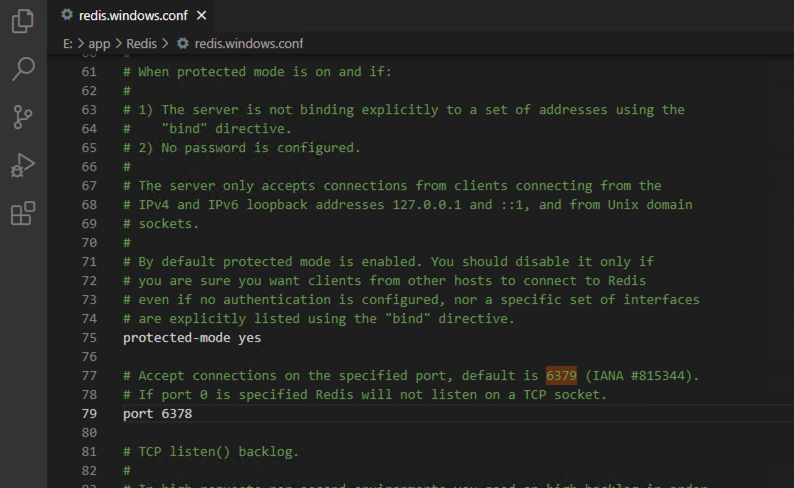
修改默认端口
不使用redis的默认端口6379
禁用或者重命名危险命令
JS
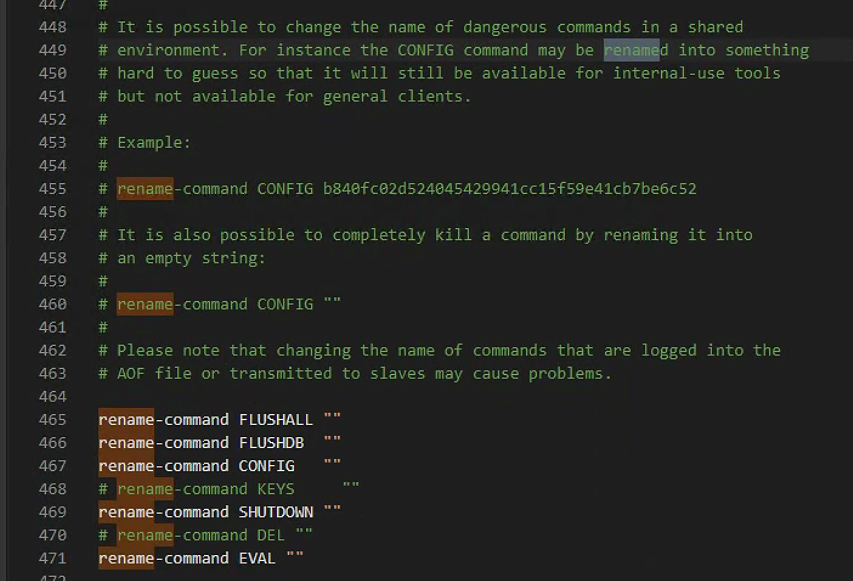
rename-command FLUSHALL ""
rename-command FLUSHDB ""
rename-command CONFIG ""
rename-command KEYS ""
rename-command SHUTDOWN ""
rename-command DEL ""
rename-command EVAL ""部分指令有使用到:keys;del配置上无法启动
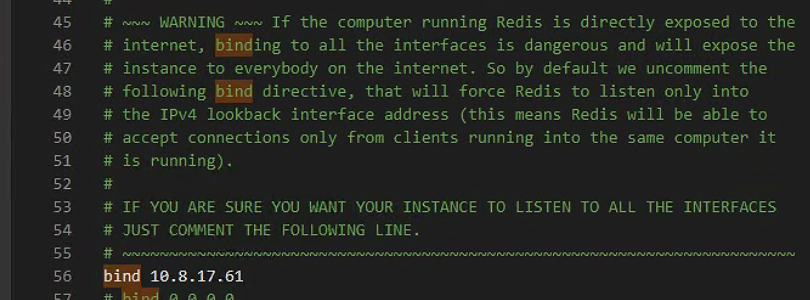
禁止公网监听
设置为制定连接ip
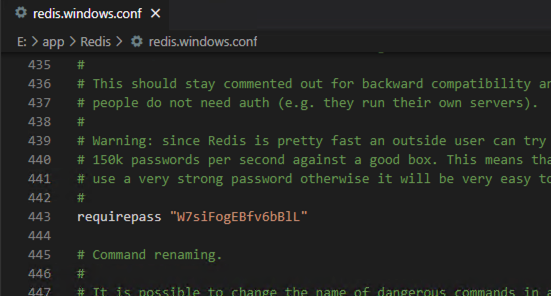
设置密码
设置连接密码,密码要设置一定复杂度
限制Redis配置文件访问权限
修改文件的安全中用户的读写权限
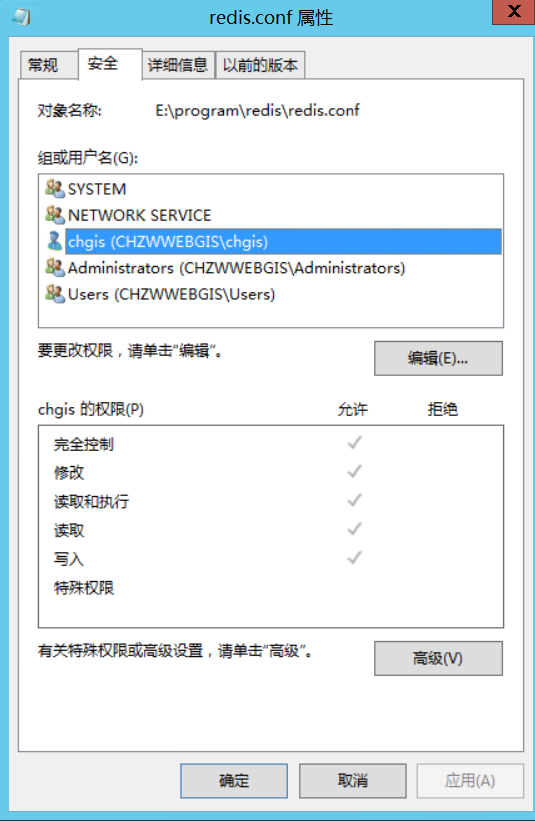
保护模式

Nginx
修改默认端口
不使用的默认80端口,如果已经是历史项目,这个也需要和业主商量
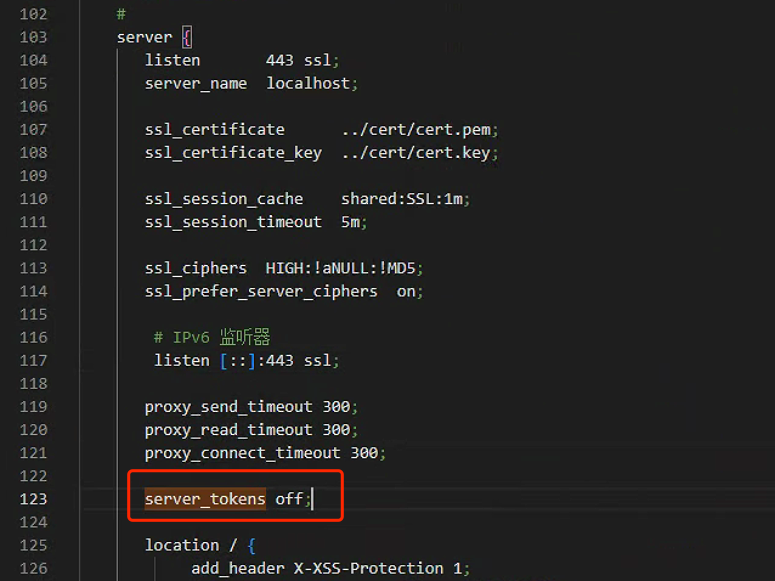
禁止显示版本信息
配置文件中添加Server_tokens参数,并设置值为off
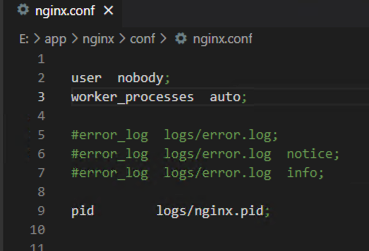
禁止非特权用户启动服务
- 查看nginx.conf文件中user参数是否配置了nobody用户
- 在操作系统控制台输入:ps aux |grep nginx
- 启用Nginx的worker process进程执行用户nobody
未设置响应头
- 未设置X-Content-Type-Options响应头
- 未设置X-XSS-Protection响应头
- 未设置Strict-Transport-Security响应头
- 点击劫持:无X-Frame-Options头信息
- 未设置Referrer-Policy响应头
- 未设置X-Download-Options响应头
- 未设置X-Permitted-Cross-Domain-Policies响应头
- 未设置Content-Security-Policy响应头
yml
add_header X-XSS-Protection 1;
add_header X-Frame-Options DENY;
add_header Cache-Control no-cache;
add_header X-Content-Type-Options nosniff;
add_header Referrer-Policy "no-referrer-when-downgrade";
add_header X-Download-Options "noopen" always;
add_header X-Permitted-Cross-Domain-Policies "master-only";
add_header Strict-Transport-Security "max-age=63072000; includeSubdomains; preload";
add_header Content-Security-Policy "script-src 'self' 'unsafe-inline' 'unsafe-eval' blob: data: ;";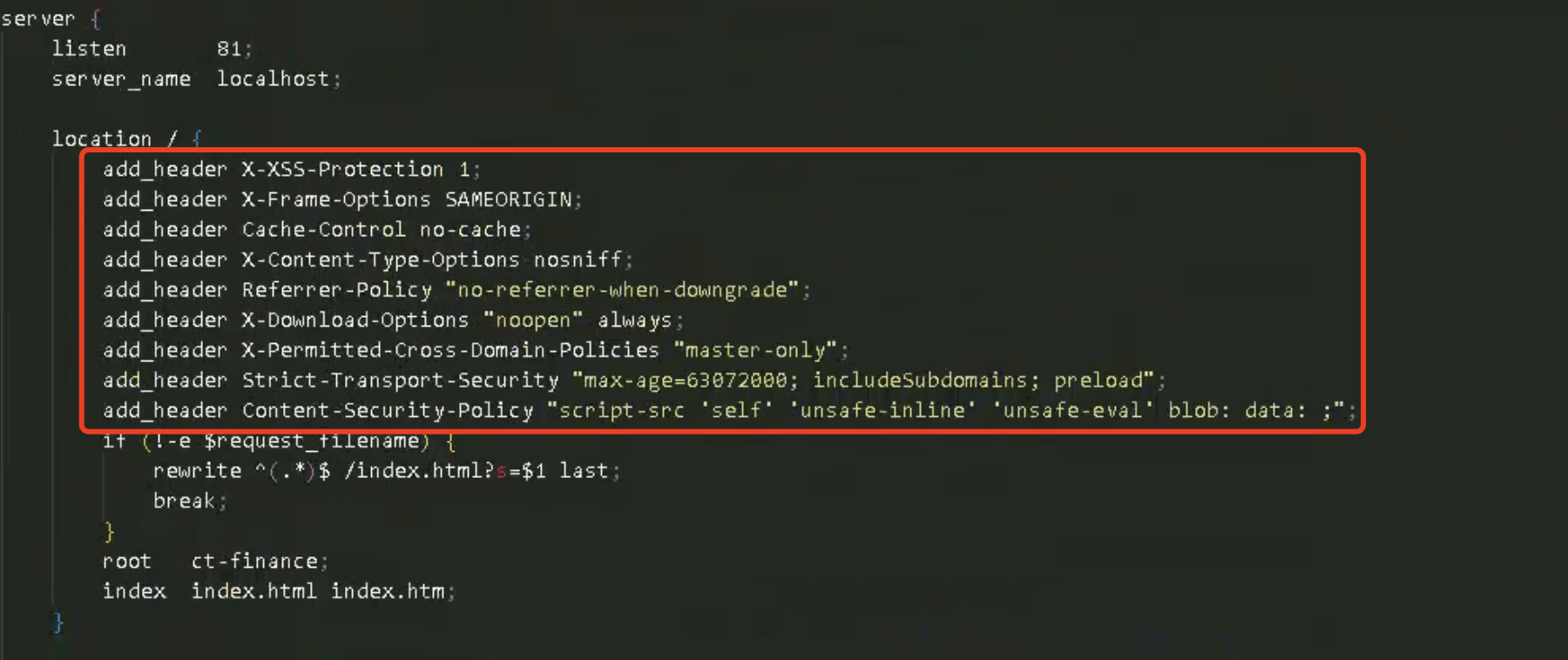
SSL RC4 加密套件支持检测 (Bar Mitzvah)
yml
ssl_ciphers "ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-AES256-SHA:ECDHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES128-SHA256:DHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES256-GCM-SHA384:AES128-GCM-SHA256:AES256-SHA256:AES128-SHA256:AES256-SHA:AES128-SHA:DES-CBC3-SHA:HIGH:!aNULL:!eNULL:!EXPORT:!DES:!MD5:!PSK:!RC4";
ssl_prefer_server_ciphers on;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
SSL/TLS协议信息泄露漏洞(CVE-2016-2183)
yml
ssl_ciphers "ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-AES256-SHA:ECDHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES128-SHA256:DHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES256-GCM-SHA384:AES128-GCM-SHA256:AES256-SHA256:AES128-SHA256:AES256-SHA:AES128-SHA:DES-CBC3-SHA:HIGH:!aNULL:!eNULL:!EXPORT:!DES:!MD5:!PSK:!RC4";
ssl_prefer_server_ciphers on;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;SSL/TLS 受诫礼(BAR-MITZVAH)攻击漏洞(CVE-2015-2808)
经验RC4
yml
ssl_ciphers "ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-AES256-SHA:ECDHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES128-SHA256:DHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES256-GCM-SHA384:AES128-GCM-SHA256:AES256-SHA256:AES128-SHA256:AES256-SHA:AES128-SHA:DES-CBC3-SHA:HIGH:!aNULL:!eNULL:!EXPORT:!DES:!MD5:!PSK:!RC4";
ssl_prefer_server_ciphers on;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;